KingFisher is an insecure shared credential (SC) detection framework against real-world IoT products, designed to automate the tasks of SC extraction and SC security inspection.
It employed a value-based data flow analysis to track SCs in IoT (Android) companion apps, and the understand how the SCs are used and inspect their security status by dynamic interaction testing.
KingFisher is currently built with a set of python scripts, combined with Frida dynamic code instrumentation framework, composed of four main components: Function Interface Identification, Message Collection, Value-based SC Extraction and Security Violation Detection.
We use KingFisher to evaluate eight IoT products, including BroadLink, Haier, Horn, Qihoo, Tuya, Xiaomi, Xiaoyi and ZTE, and discover their vulnerable SC usage and implementations.
So far, we have received five CNVDs (i.e., CNVD-2021-73144, CNVD-2021-90790, CNVD-2021-90791, CNVD-2021-39530, CNVD-2021-73145, CNVD-2021-73140, CNVD-2021-90647, CNVD-2021-73142) and one is waited for confirmation.
Huawei replied that they have internally isolated the device registration process (SC generation and distribution) of new devices that support another more secure protocol and old devices that can not be updated to new protocols.
And we will help them and horn company to deploy the patch to deal with the issues.
We have implemented KingFisher with Python and JavaScript scripts, combining and integrating some other tools: Frida dynamic code instrumentation framework, tcpdump packet capture binary and Burp Suite toolkit for web security testing.
The code files of KingFisher and their introduction are listed as below.
| Files | Details |
|---|---|
| identify_java_funcs.py | Identifying SC-related functions in Java code and generate corresponding instrumentation scripts. |
| identify_native_funcs.py | Identifying SC-related functions in Native code and generate corresponding instrumentation scripts. |
| collection.py | Collecting Message. |
| extract_SC.py | Implementing value-based analysis to extract possible SCs from collected messages. |
| violation_detection | Detecting if the products violate security property and including nine independent tests. |
KingFisher adopts keyword-based search for function recognition. We observed that most SC related functions are sensitive functions, e.g., cryptographic functions, data construction functions, and network related functions. In particular, cryptographic functions take as input the CSC as an encryption key to encrypt the transmission data. The encrypted data and some other information are format as a transmission message by data construction functions and further transmitted over the communication channel by network related functions.
We manually construct a reference set from source code of Github and StackOverflow, which contains a list of keywords that are commonly used to name SC-related functions.
The reference set is listed as following. And by the reference set, we identify the potentially SC-related functions, and output a SC function candidates list.
Note the asterisk indicates zero or more occurrences of any characters.
An example of the Function Interface Identification result is listed as following:
{
"class": "com.tuya.sdk.hardwareprotocol.control.LocalControl3_2",
"method": "encryptRequestWithLocalKey",
"params": [
"com.tuya.sdk.hardwareprotocol.bean.HRequest",
"java.lang.String",
"java.lang.String"
],
"params_len": 3,
"return": "com.tuya.sdk.hardwareprotocol.bean.HRequest"
}
Code Demo: com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey(com.tuya.sdk.hardwareprotocol.bean.HRequest, java.lang.String, java.lang.String): com.tuya.sdk.hardwareprotocol.bean.HRequest
var com_tuya_sdk_hardwareprotocol_control_LocalControl3_2 = Java.use("com.tuya.sdk.hardwareprotocol.control.LocalControl3_2");
com_tuya_sdk_hardwareprotocol_control_LocalControl3_2.encryptRequestWithLocalKey.overload("com.tuya.sdk.hardwareprotocol.bean.HRequest","java.lang.String","java.lang.String").implementation = function(s0, s1, s2){
console.log("----------------------------com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey---------------------------");
console.log("[s] com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey argument 0 = " + s0 + " [e]");
console.log("[s] com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey argument 1 = " + s1 + " [e]");
console.log("[s] com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey argument 2 = " + s2 + " [e]");
var res = this.encryptRequestWithLocalKey(s0, s1, s2);
console.log("[s] com.tuya.sdk.hardwareprotocol.control.LocalControl3_2.encryptRequestWithLocalKey res = " + res + " [e]");
console.log("++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++");
return res;
}
Code Demo: __int64 __fastcall tuya::BizLogicService::SendByte(_QWORD *a1, unsigned __int8 *a2, __int64 a3, unsigned int a4, __int64 a5, __int64 a6)
var a1 = new Array()
Interceptor.attach(
Module.getExportByName("libnetwork-android.so", "_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE"), {
onEnter: function(args) {
console.log("----------------------------libnetwork-android.so-_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE---------------------------")
a1 = new Array()
for(var i = 0; i < 10; i++){
var ar = Process.findRangeByAddress(args[i])
if(ar != null && ar['protection'] == 'rw-'){
var ad = parseInt(args[i])
var arstr = ''
for(var j = 0; j < 256; j++){
var ch = (ptr(ad+j).readU8()).toString(16)
if(ch.length < 2) ch = '0' + ch
arstr = arstr + ch
}
console.log("[s] libnetwork-android.so-_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE argument " + i + " = " + arstr + " [e]")
var ii = {"ind":i,"point":args[i]}
a1.push(ii)
}
}
},
onLeave: function(retval){
for(var i=0; i < a1.length; i++){
var ad = parseInt(a1[i]['point'])
var arstr = ''
for(var j = 0; j < 256; j++){
var ch = (ptr(ad+j).readU8()).toString(16)
if(ch.length < 2) ch = '0' + ch
arstr = arstr + ch
}
console.log("[s] libnetwork-android.so-_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE res-argument " + a1[i]['ind'] + " = " + arstr + " [e]")
}
if(Process.findRangeByAddress(retval) != null){
var rd = parseInt(this.retval)
var rstr = ''
for(var j = 0; j < 256; j++){
var ch = (ptr(rd+j).readU8()).toString(16)
if(ch.length < 2) ch = '0' + ch
rstr = rstr + ch
}
console.log("[s] libnetwork-android.so-_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE res = " + rstr + " [e]")
}
else console.log("[s] libnetwork-android.so-_ZN4tuya15BizLogicService8SendByteEPhliNSt6__ndk112basic_stringIcNS2_11char_traitsIcEENS2_9allocatorIcEEEENS2_8functionIFviiPKhiEEE res = " + retval + " [e]")
console.log("++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++");
}
}
);
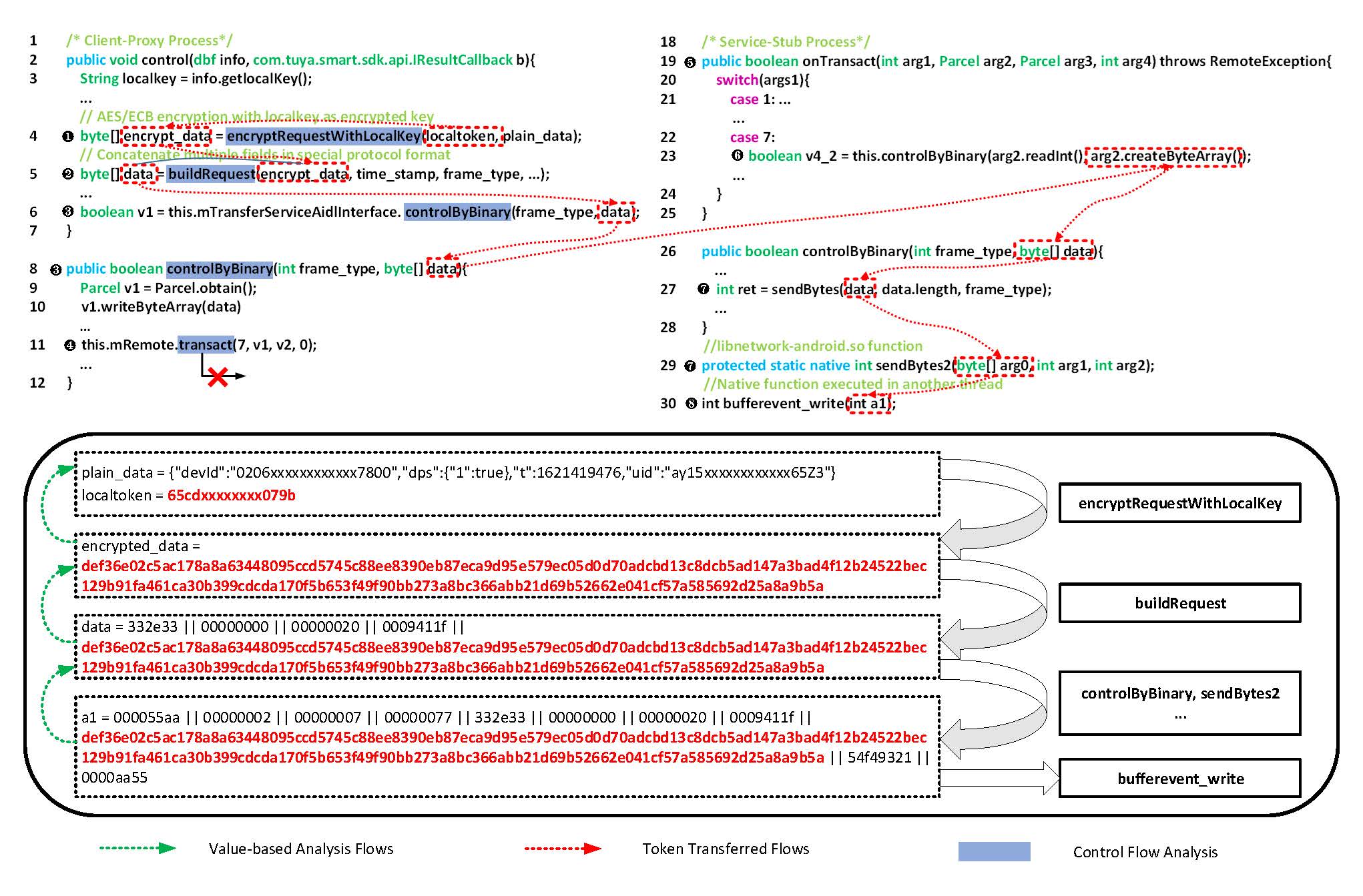
Taken Function Value Collection and Traffic Clustering results as input, KingFisher executes a value-based analysis in two steps to distinguish the used SCs. We illustrate the detailed Tuya example in the figure below to explain how the value-based analysis works and why common program analysis methods (e.g., control flow construction) could not be applied in our approach.

bufferevent_write, sendBytes2, controlByBinary, buildRequest and encryptRequestWithLocalKey functions will be marked as Key_Fun.
KingFisher next assesses the security of the SCs based on the security properties listed in Section 3. Specially, the SC used in this procedure is the correct one after verification. And the security violation detection tests for nine properties are independent, so than each test could be done separately.
The source code of the security violation detection will be available soon.
Take Tuya as an example, the step by step tutorials of how KingFisher analyze a IoT product (i.e., an IoT device and its companion app) are provided as below.
pip install frida and pip install frida-tools
Check frida client version: frida --version
Download corresponding version and architecture (decided by the Android smartphone) frida server and push it to smartphone.
./frida-server
python identify_xxx_funcs.py
tcpdump -i {Network Interface Name} -w {Pcap Files Output Path}
python collection.py
python extract_SC.py
python violationx_detect.py
x is the index of security property.
The evaluation dataset of our experiment is available: dataset. It includes the experimental objects (i.e., eight IoT companion apps downloaded from Google Play and Tencent Myapp) and the our SC extraction results (i.e., SC Function Candidate Listlocated interfaces, Function Information List, Key_Fun and Related_Func).
Our experiment covers eight IoT vendors:
| IoT Vendor | SC-related Functions | SCs | ||
|---|---|---|---|---|
| Java | Native | ASC | CSC | |
| BroadLink | 2d07905f0fcc2919f290c3526ab4cd49 | |||
| Haier | 7y5INpxqLQKHmdo0wUd7V8R2k9gp2xR1SZdISl6t: eCgrgL9M-5HdKH4yw-RB5LP0sI8=: eyJyYW5kb20iOjE2MjE1ODc3ODM2MjYsInN0YXRlbWVudCI6W3siY WN0aW9uIjoibGlua2luZzp0dXRrIn1dLCJkZWFkbGluZSI6MTYyMTU5MTM4M30= |
|||
| Horn | 9205B304FD64482D >6e4d397472546231 |
|||
| Qihoo | 54f4281b3738d2ea56c68c873a7ecc40655986f8e21260a1c0289a54cdb7d167 | 54f4281b3738d2ea56c68c873a7ecc40655986f8e21260a1c0289a54cdb7d167 | ||
| Tuya | 65cda52393a0079b | |||
| Xiaomi | d8e7b8fa1a569d8ede2e890aa850c02e | |||
| Xiaoyi | UrFvIGY7DfoIIan | UrFvIGY7DfoIIan | ||
| ZTE | CiV6vk1WE4MsvsPT | |||
| IoT Vendor | Device | Companion App | Confirmed | |
|---|---|---|---|---|
| Type | Model | |||
| BroadLink | Smart Plug | SP 4L | cn.com.broadlink.econtrol.international | Yes (CNVD-2021-73144) |
| Haier | Smart Camera | HCC-22B20-W | com.haier.uhome.uplus | Yes (CNVD-2021-90790, CNVD-2021-90791) |
| Horn | Smart Gateway | T2 | com.huawei.smarthome | Yes (CNVD-2021-39530) |
| Qihoo | Smart Camera | AP5CA1 | com.qihoo.camera | Waiting |
| Tuya | Smart Plug | YKYC-W1Y0-16 | com.tuya.smart | Yes (CNVD-2021-73145) |
| Xiaomi | Smart Gateway | DGNWG02LM | com.xiaomi.smarthome | Yes (CNVD-2021-73140) |
| Xiaoyi | Smart Camera | YHS-113 | com.ants360.yicamera | Yes (CNVD-2021-90647) |
| ZTE | Smart Camera | C320 | com.ztesoft.homecare | Yes (CNVD-2021-73142) |
"Waiting" means we have reported to the IoT vendor and waited for confirmation.